The United States is home to more than 2.8 million miles of natural gas and hazardous liquid pipelines, which are operated by over 3 thousand private companies from across the country. These assets that run through America have grown so vast in size, they are susceptible to attacks from both physical attacks and cyber intrusions.
This article will introduce digital checklists that industries can utilized to conduct structured assessments of both facility and cyber assets security based on recent TSA (Transportation Security Administration) Pipeline Guidelines.
Table of Contents:
1. Introduction to TSA Pipeline Security Guidelines
2. Facility Security Measures with FAT FINGER
3. Pipeline Cyber Asset Security Measures with FAT FINGER
Introduction to TSA Pipeline Security Guidelines
TSA’s Pipeline Security Guidelines are designed to protect pipeline infrastructure against known and emerging threats. TSA’s Office of Security Policy and Industry Engagement’s Surface Division has repeatedly published updated iterations of the Pipeline Security Guidelines as the agency works with operators to address known and emerging threats against millions of miles of pipeline infrastructure and proprietary operations.
Since 2010, TSA is at the forefront of efforts domestic oil and gas infrastructure under the initial version of Pipeline Security Guidelines. Protecting against new threats and staying on top of constantly changing security guidelines, TSA subsequently published succeeding developments:
-2011 Guidelines, second iteration
-2011, “Pipelines Security Smart Practice Observations”

-2018, Guidelines, third iteration
-2021, Security Directives 1 & 2
-2021, Pipeline Security Guidelines, fourth and current iteration
Agile solutions allow TSA together with the domestic oil and gas industry to quickly adapt to the latest threats and stay ahead of constantly shifting security guidelines. In the latest 2021 version, the TSA issued updates to its Pipeline Security Guidelines, providing guidance for critical facilities.
Critical facilities may include, but are not limited to:
-pipeline interconnections
-metering and/or regulating stations
-pump stations
-compressor stations
-operational control facilities
-main line valves
-tank farms, terminals
Facility Security Measures with FAT FINGER
The TSA Pipeline Security Guidelines recommend that pipeline operators develop, document, and implement site-specific security measures for each of their critical facilities.
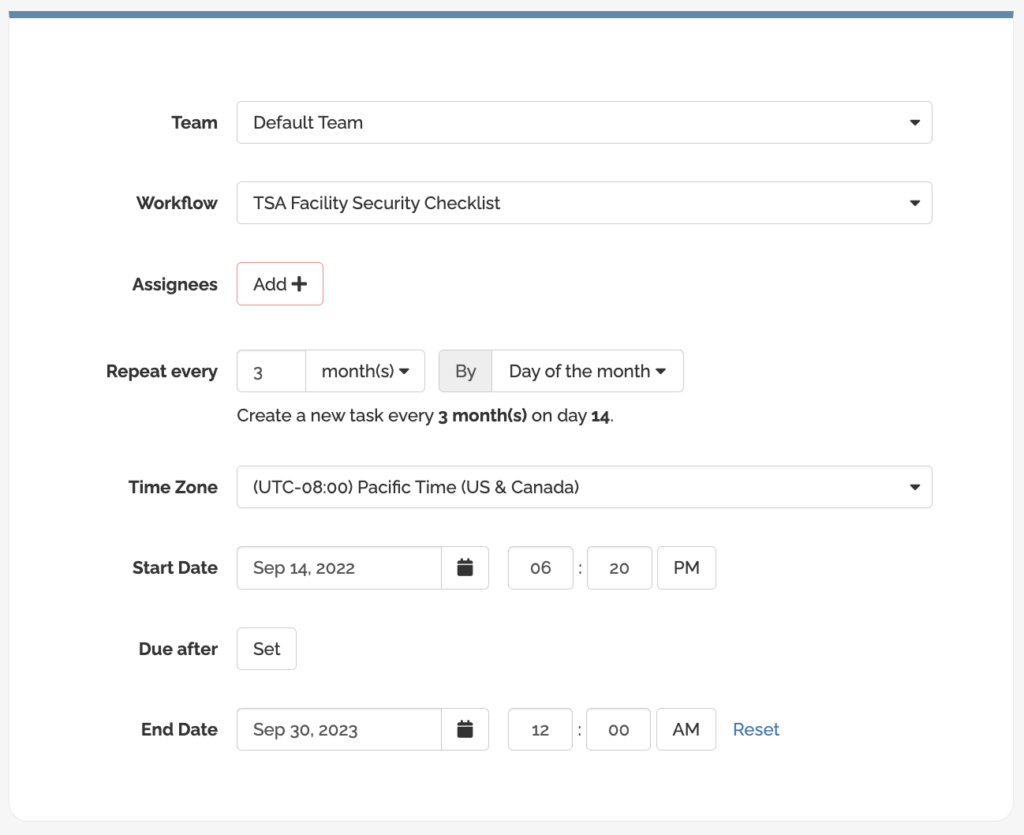
Some key considerations for developing effective security measures include: identifying critical assets and vulnerabilities, assessing the threat environment, implementing physical security measures, and developing emergency response plan on a periodic basis not to exceed 18 months.

Facility security is a critical issue, but it’s hard to know where to start. There are so many things to consider when assessing the security of a critical facility – from the personnel securities, to the pipeline designs and construction, to equipment maintenance and testing. It can be hard to know where to start.
FAT FINGER is the solution you need to properly assess and secure your critical facilities. FAT FINGER comprehensive digital facility security checklist will help you identify vulnerabilities and threats, so that you can take appropriate action to mitigate them.
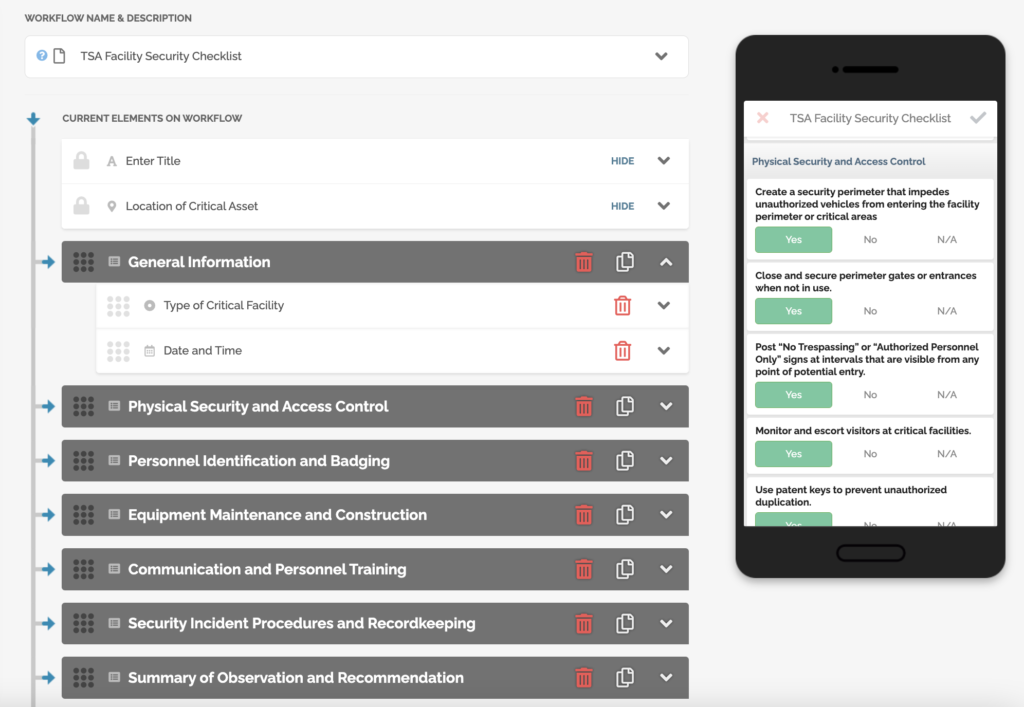
From physical security and access control checklist to digital and accessible record keeping, you can be sure that no stone is left unturned in your search for safety and protection.
Plus, FAT FINGER reminds you when it’s time for your next assessment so you can rest easy knowing you’re on track.
TSA’s goal is to provide a regulatory framework within which pipeline operators can craft comprehensive security programs that reflect the unique characteristics of their individual operations.
FAT FINGER recognizes that one size does not fit all when it comes to security that’s why our digital checklist can be customized depending on your site-specific security measures.
Pipeline Cyber Asset Security Measures with FAT FINGER
Operators use many different types of cyber assets in their pipelines to help manage and monitor the safe and efficient operation of their systems. These cyber assets include control systems (SCADA, process control systems (PCS), distributed control systems (DCS)), measurement systems and telemetry systems. Each of these cyber assets provides vital information that helps the operator to make informed decisions about the pipeline system. The cyber assets also provide the operator with a means to remotely control and monitor the pipeline system.
The most recent TSA security directive (Second Directive) was deemed sensitive and kept secret from the general public.What is known about the Second Directive is that it requires pipeline firms to implement mitigation strategies to prevent cyberattacks and establish a cybersecurity contingency and recovery plan for cyber assets. These new regulatory cybersecurity standards are backed up by penalties that can reach $11,904 per day, per non-compliance.

Cybersecurity is a critical issue for all organizations, but many don’t have the resources to properly assess and secure their cyber assets. A cyber attack can cripple natural gas companies and the like, costing them time, money, and reputation. FAT FINGER provides comprehensive cyber assets assessment checklists based on latest TSA Pipeline Security guidelines which help organizations identify and fix vulnerabilities before any unforeseen circumstances arise.
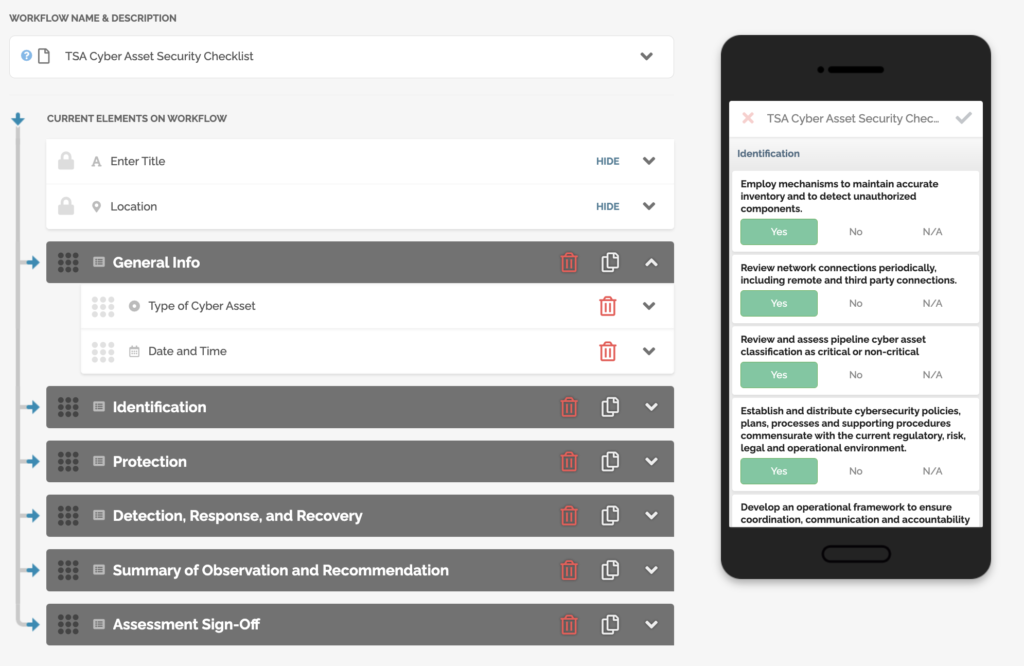
FAT FINGER cyber asset security assessment checklist will improve your risk management, help you identify and prioritize threats and vulnerabilities, streamline remediation processes, and elevate your cyber asset security through this proactive approach.
Through FAT FINGER mobile app, pipeline operators and cyber assets security professionals can maximized this powerful checklist to:
- Easily revise and disseminate checklists when the cyber asset security plan is updated
- Generate user-friendly cyber asset security assessment reports to track the standing of cyber assets security program
- Sign off cyber asset assessment checklist with management and other key stakeholders
- Schedule periodic reviews
Don’t leave your business vulnerable – opt for a security solution that allows for customizations and seamless integrations today!
FAT FINGER offers a suite of customizable workflows that allow for seamless integrations with other security systems, so you can be confident that your critical assets are protected and compliant with TSA Pipeline Security Guidelines.
About FAT FINGER:
Ensure front-line teams do their work correctly every time. Drag & drop digital procedures that unlock operational excellence.
In seconds anyone can build and deploy enterprise-grade mobile applications using an easy drag-and-drop no-code builder.
FAT FINGER uses machine learning to coach app users in real-time to make safer and improved decisions.
Try building your digital procedure on FAT FINGER for free @ www.fatfinger.io